Events to Actions
Avalannchio rule engine detects complex event patterns and takes automated actions.
Avalannchio rule engine detects complex event patterns and takes automated actions.
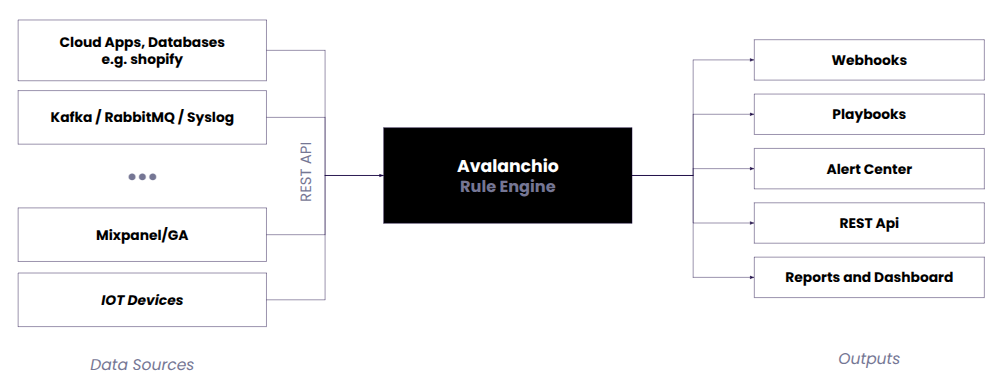
Remote agents collect data from devices, existing log tools or various endpoints and send them to Avalanchio in real-time.
Extract required features from the events and define rules using SQL and various other techniques to detect simple to advanced patterns.
Send incidicators to alert center for further investigation, call webhooks, run playbooks or simply send alert notifications.

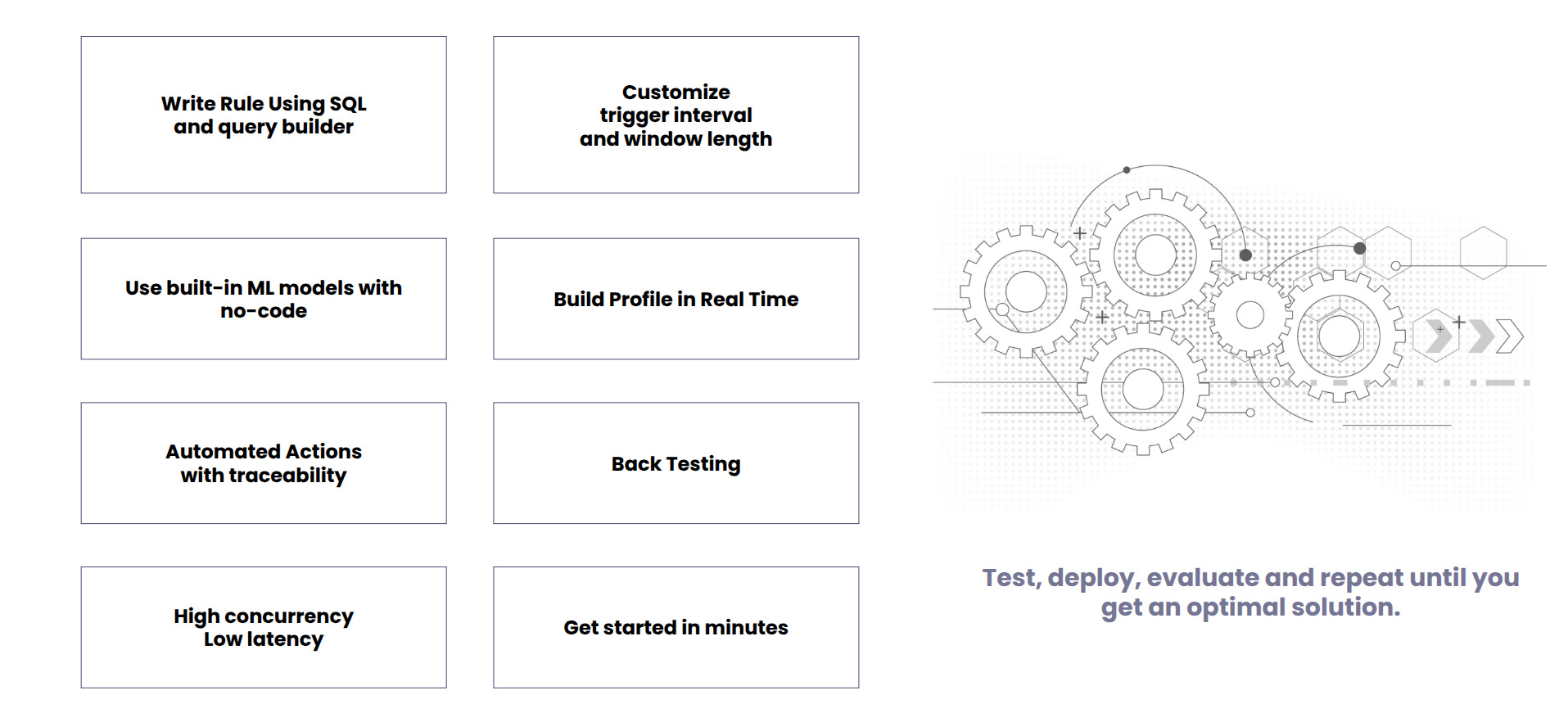
Express your business logic using SQL or query builder - the rules run continuously as the event data arrives. Refine results using several built-in layers of techniques such anomaly detection, rarity analysis.
Run thousands of queries per day with as low latency as low as a few milliseconds.
Automate actions as soon as some patterns are detected from the events. Send alerts, run playbooks, invoke web hooks etc.or simply accumulate the output to a table to query through REST api.
Re-run a rule on historical events to test a hypothesis. Users' feedbacks are used to curb false alarms using a built-in ML model.
Rule engine analyzes data in real-time, continuously builds data profiles, triggers automate actions as soon as specified patterns are detected in the events.
Use SQL statements to filter targeted events or prepare enriched datasets.
Define rule using sigma rule format. It makes it easy to integrate with rules maintained by open source community.
Run the rules against real time data stream with response time as low as a few seconds.
Rule engine can execute thousands of rules against large data volume with less hardware using a purpose built engine.

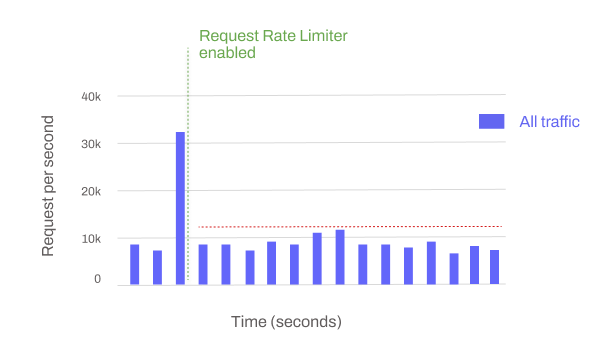
Preventing abuse, overuse, and ensuring fair usage of resources using rate limiter
Control the rate at which clients can make requests to certain resources.
Sets limits on the number of requests within a specified timeframe
Trigger controls to throttle rate of requests or block requests completely.
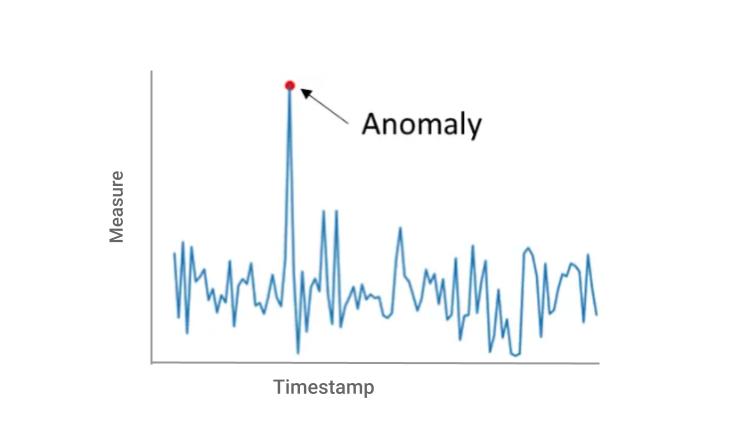
Detects anomalies using built-in anomaly detection techniques.
Techniques such as isolation forest, one class SVM, local outlier factor, Histogram-based Outlier Detection (HBOS) to name a few.
No-code is required
Majority of the algorithms are unsupervised. Hence, they start working as soon as you on-board data.
Run remediation playbooks. Use one of built-in playbooks or create your own easily using Python script to take action when a certain event conditions are met.
Run webhooks to call any third party endpoints, for example, to trigger a workflow.
Send notifications via email.
Agents collect data from your local data center, existing log tools or REST endpoints.
Define rules using SQL. Run the rules in near realtime to detect complex patterns.
Send events data to alert center, call webhooks, run playbooks etc.